Nick Johnson, that indefatigable Ethereum Name Service engineer with a nose for digital skulduggery, has unmasked a phishing escapade so artful it might have won a turn at the Savoy cocktail party. This little adventure exploited a recently patched OAuth quirk in Google’s own implausibly large fortress of security.
Google’s Fortitude Takes a Holiday: ENS Engineer Unearths Phishing Shenanigans
According to Johnson’s chronicle of woe and wonder, the ruse began with an email that bore all the charm and menace of a dreaded official Google alert. It warned unlucky recipients of an impending subpoena demanding their account secrets—signed with real DKIM flair and shot forth from Google’s own no-reply bastion. Gmail’s filters? They simply bowed in obeisance and allowed it through like a guest with a written invitation.
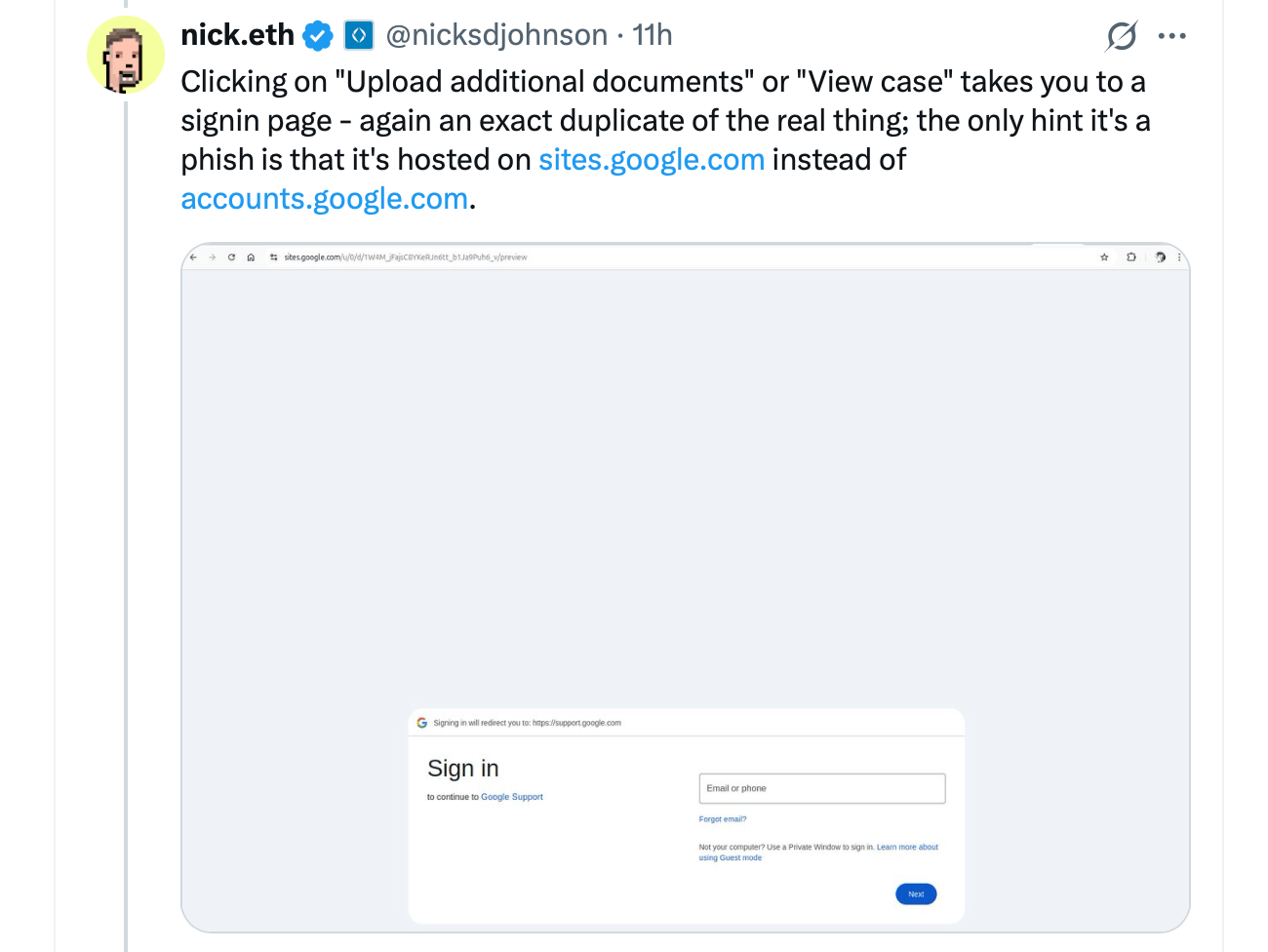
Johnson further observed that the scam’s credibility was hand-polished by a hyperlink to sites.google.com, leading to a spurious support portal that replicated Google’s login page with such fidelity it would make a master forger blush. The con hinged on two particular softnesses: Google Sites’ permissiveness toward arbitrary scripts, gifting villains the means to harvest credentials, and that now-infamous OAuth vulnerability.
With the grace of a debutante at her first ball, the attackers procured a fresh domain, daintily opened a Google account, and concocted an OAuth app whose nomenclature obediently mirrored the phishing email’s menacing title. Once the mark—sorry, victim—handed over access, Google, unaware it was aiding the enemy, generated fully signed, authentic-seeming security alerts which the miscreants then paraded before their prey. A virtuoso performance of digital duplicity.
Johnson took no pains to conceal his disdain for Google’s initial shrug, dismissing the bug as “working as intended.” To which one might reply: so is a fox in the henhouse, but one hardly supposes it a good thing. Alas, the scam’s use of the venerable sites.google.com domain further beguiled users into mistaking the wolf for a cuddly creature. Google’s sluggish abuse reporting system for Sites compounded the issue, turning takedown efforts into a waltz of frustration.
Following a crescendo of public outcry, Google performed a rare volte-face and accepted the problem’s existence. Johnson confirmed that the tech titan is at last preparing a fix for the OAuth misstep. This spectacle lays bare phishing’s mounting sophistication as it pirouettes on the labyrinthine defenses of the internet’s most illustrious institutions.
Meanwhile, security savants advise that users adopt the modest habit of questioning unexpected legal-sounding communiqués and scrutinizing URLs before surrendering their sacred credentials. Google has been notably reticent on matters of public bulletin regarding the flaw’s timetable for obliteration. This episode, replete with guile and gall, reminds us that the battle against phishing rogues is less a sprint and more a dismal, relentless marathon.
🔍💼💀
Read More
- PI PREDICTION. PI cryptocurrency
- Gold Rate Forecast
- WCT PREDICTION. WCT cryptocurrency
- LPT PREDICTION. LPT cryptocurrency
- Guide: 18 PS5, PS4 Games You Should Buy in PS Store’s Extended Play Sale
- Solo Leveling Arise Tawata Kanae Guide
- Despite Bitcoin’s $64K surprise, some major concerns persist
- Clarkson’s Farm Season 5: What We Know About the Release Date and More!
- Planet Coaster 2 Interview – Water Parks, Coaster Customization, PS5 Pro Enhancements, and More
- Chrishell Stause’s Dig at Ex-Husband Justin Hartley Sparks Backlash
2025-04-17 00:27